Learn Why Keybase.io is Awesome!
With the recent success of Zoom and their recent purchase of Keybase... they're set to bring authenticated encryption to the masses.

It's likely you have never heard of Keybase.io, but I'm guessing that you soon will!
I'm going to cover a few basic concepts of Keybase and cryptography - in less than 500 words.
- Public Keys
- Malleable Encryption
- Authenticated Encryption
With the recent success of Zoom and their recent purchase of Keybase... they're set to bring authenticated encryption to the masses.
This acquisition has been concerning to some, but Keybase is open source, so I consider the issue analogous to when Twitter bought Signal.
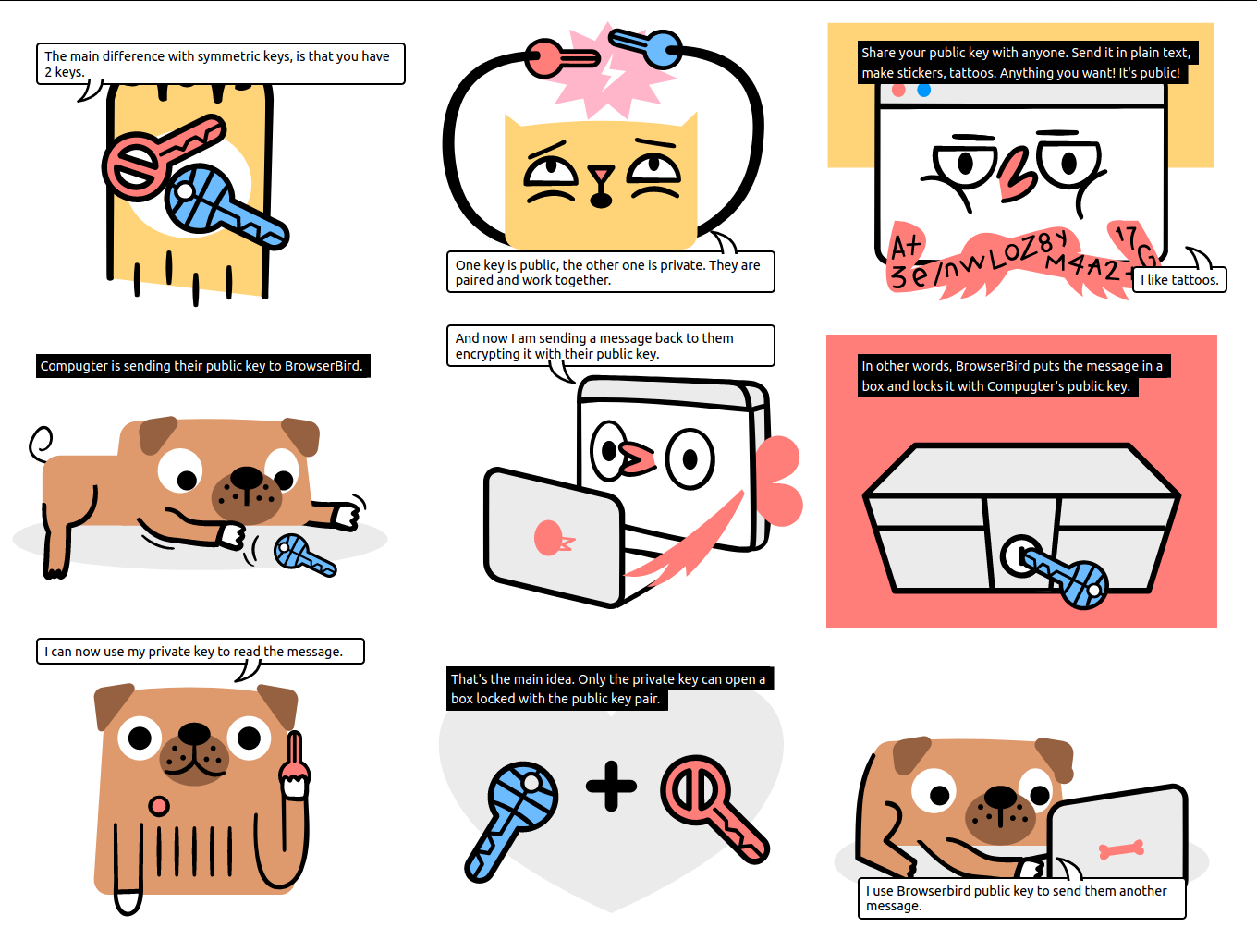
Public Keys
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys, which may be disseminated widely, and private keys, which are known only to the owner.
- The Public Key is used to encrypt a message that can only be read by the Private Key. You already use this technology every day. This website is encrypted with HTTPS!
Look for https:// in your address bar anytime you send sensitive data!!!
Public Key Cryptography was first discovered by the British Government and kept secret until Diffie and Helman brought it to the public - a fascinating story!
Without this discovery the internet would not be very secure because all encryption would require sharing a key over a secure channel like in person contact.
whoami?
Keybase makes public keys out of everything, sortof.
If you want to send me an encrypted message, but only have my Facebook, you can use Keybase to send me a message using my Facebook name. I can revoke that link if my Facebook get's hacked~
So far, there is no silver bullet for authentication in our post modern technological civilization. But, Keybase will bring great gains.
You should be using a Password Manager. Regardless of anything else, do that!!!
Two types of encryption
Encryption can be malleable (Signal), or not (PGP, Keybase). Not a matter of good, bad, or better - it's a matter of usecase.
Malleability is a property of some cryptographic algorithms. An encryption algorithm is "malleable" if it is possible to transform a ciphertext into another ciphertext which decrypts to a related plaintext.
Malleability == Changeability
Malleable Encryption offers plausible deniability, but that's not ideal for every use case.
Authenticated encryption (AE) and authenticated encryption with associated data (AEAD) are forms of encryption which simultaneously assure the confidentiality and authenticity of data.
Often, we want proof that a communication happened exactly as we have it recorded. This has been possible for years with PGP, and Keybase now brings authenticated communication to everyone!
If you are doing illegal things Keybase might not be ideal. Consider when PGP (authenticated encrypted) communication with police led to the downfall of the Silk Road. There are however "self destructing" messages in Keybase, which "deletes" messages with forward secrecy so that nobody can every read them again.
Techy?
Keybase uses Saltpack. If you already know about PGP you will enjoy reading about it.





